Azure Active Directory B2C is an access management solution offered by Microsoft, designed to help companies manage the identities of their customers. This platform allows organizations to offer personalized and secure login experiences through a series of tools and functionalities that facilitate user registration, access and management, all with a flexible configuration that adapts to the specific needs of each reality. In this article, we'll take a closer look at what B2C is, how it works, and what factors influence service costs.

Identity and access management (IAM) is a fundamental aspect of modern businesses. It ensures that only authorized users have access to sensitive information and resources, while ensuring that users can easily access the resources they need to do their jobs.
Effective Identity Access Management helps businesses reduce security risks, improve compliance, and increase productivity. It's essential for protecting sensitive data and applications, especially in the era of remote work and cloud computing.
Azure B2C is a CIAM solution that allows businesses, governments and other organizations to offer their customers and partners access to their web and mobile applications. Users can use their preferred social identity, corporate identity, or local accounts for single sign-on (SSO) access to a wide range of applications and APIs.
It is essential that users know that they are interacting with their service and not that they are directed to enter their personal information on a third-party platform. With Azure B2C, the entire experience can be customized to meet business needs, brand image, and messaging. The strength of Azure B2C lies in the Microsoft Identity Experience Framework (IEF), a powerful tool that orchestrates almost any authentication service, user registration, profile modification, or account recovery.

Before continuing to talk about Azure B2C, it is important to understand the main concept on which it is based: CIAM, which stands for Customer Identity and Access Management.
It is quite simply a solution used by companies and organizations to effectively manage and protect the personal information of their customers.
Think about all the online services you use, such as social media, online shopping, or gaming platforms. When you create an account, you usually provide personal details such as your name, email, and possibly date of birth or telephone number. This information allows the services to recognize you and offer you personalized experiences.
CIAM employs various methods to protect your personal information. It allows you to create a secure username and password combination and can also incorporate additional security measures such as two-factor authentication, where you must provide extra information, such as a code sent to your phone in order to log in.
We have created the Infrastructure & Security team, focused on the Azure cloud, to better respond to the needs of our customers who involve us in technical and strategic decisions. In addition to configuring and managing the tenant, we also take care of:
With Dev4Side, you have a reliable partner that supports you across the entire Microsoft application ecosystem.
Azure AD B2C is a CIAM solution that can support millions of users and billions of authentications per day. It manages the scalability and security of the authentication platform, automatically monitoring and dealing with threats such as denial-of-service attacks, password spray or brute force. In a nutshell, it is a service that manages the identities and permissions of identified users to allow them to access the services offered by their product.
B2C is separate from Azure Active Directory (Azure AD) and, although based on the same Azure AD technology, it has different objectives, being in fact created to manage the user base of one or more applications, identify them using a set of approved identity providers and generate secure access tokens that can be used to authorize user actions within your application or service.
The service implements the OAuth 2, SAML 2.0 (authentication protocol used for business federation scenarios) and OpenID Connect protocols to provide authentication and authorization methods based on open standards.
Azure Active Directory B2C features include:
Azure Active Directory B2C is often described as a multi-tenant solution.
But what is a tenant, exactly?
A tenant is nothing more than a dedicated instance of Azure Active Directory (AD) created specifically to manage user authentication and authorization, a private and separate area that manages all the information and resources for a specific organization.

Each tenant in Azure AD is completely separate from the others, meaning that one tenant's data and resources are not accessible to other tenants. In other words, it's like having an exclusive and secure space for your organization in the vast world of the cloud.
A B2C tenant specifically allows an organization to manage access to its services and applications by external customers, rather than internal employees (as is the case with Entra ID tenants). A completely separate directory that cannot share resources, users, or permissions with the organization's Active Directory except to modify it with specific configurations.
B2C tenants are separate entities from Azure subscriptions. You can associate B2C tenants with billing subscriptions, and each B2C tenant represents a separate, autonomous directory with its own domain. “.onmicrosoft.com”.
Authentication is a fundamental security mechanism used to protect sensitive information and prevent unauthorized access to systems and data. It prevents financial losses, data breaches, and keeps your company's reputation intact. The process focuses on verifying the identity of a user, system or device, which generally involves presenting certain credentials, such as a password or a fingerprint.
In addition to the classic username and password method, Azure B2C offers various authentication methods, each of which can be used individually or in combination with other methods to optimize security and user experience while using our applications.
Let's see them in the list below:
Azure B2C also provides a series of user flows to simplify the implementation of security measures. A user flow is nothing more than a predefined process that guides users through a series of steps while interacting with their authentication and registration system and defines how users interact with the login, registration, password recovery and other identity-related operations pages.

The service provides various predefined user flows for common activities such as registration, login, password recovery and modification of user information, and each user flow guides the user through a specific set of steps, reducing difficulty and limiting the possibility of possible human errors.
User flows are configurable through the Azure portal, defining various parameters such as the fields to be collected (e.g. name, email address), authentication criteria (e.g. password or multifactor authentication) and the actions to be taken after the flow is completed, and you can customize the appearance and behavior of user flows through page templates and integration with your content, such as login and registration pages, allowing you to maintain a user experience consistent with your brand.
If, on the other hand, we find ourselves in more complex scenarios, which require greater customization or the implementation of more advanced features than those configurable with normal user flows, B2C also provides the possibility of using custom policies that can be configured through XML files.

As mentioned above, Single Sign-On (SSO) is an Azure B2C feature that allows users to sign in to multiple applications using a single set of credentials. Instead of remembering different usernames and passwords for each system, users can log in once with their preferred credentials and log in to all connected applications without having to log in again. This improves the user experience by reducing the brake and facilitating access to the necessary platform.
SSO also helps improve security by reducing the number of passwords that need to be remembered and reducing the risk of password-related security breaches. In addition, SSO helps organizations enforce password policies and ensure that the passwords used are strong and secure.
However, if you lose this single set of credentials, you will lose access to everything.
You need to keep that in mind.
When approaching Azure, it is extremely common to be confused by the enormous amount of apparently very similar services and sometimes identified by virtually identical names that can confuse those who are not familiar with Microsoft's cloud environments.
Even in the case of Azure B2C, there is no difference, so let's take a moment to clarify our ideas and distinguish the service from one of the most popular features of Active Directory: B2B.
B2B is an Azure Active Directory feature that ultimately supports employees, partners, and any internal user. The goal of B2B is to provide a system that allows shared access to business applications.
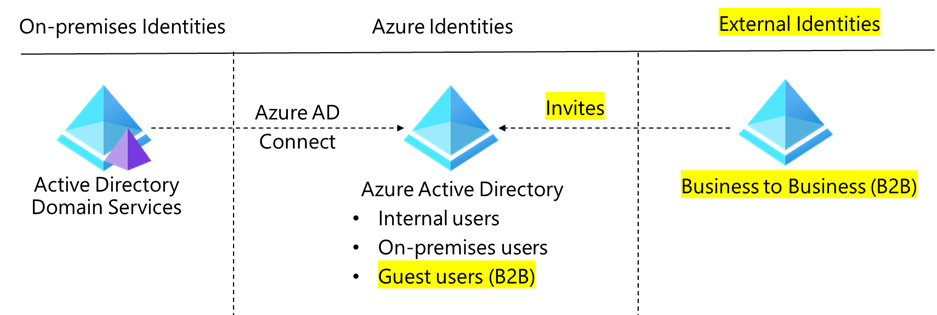
This feature is very popular precisely because of its collaborative element. With easy access for both employee and partner work accounts, regardless of their email address. The topic of easy access continues through B2B with the IDs of employees and partners managed through the same directory. This means that everyone in the directory can be added to the same groups and applications.
For some readers, the security of shared applications may be a concern, so let's dive a little deeper into the security aspect. In short, lifecycles are managed by the host or inviting organization, otherwise known as 'Azure AD B2B collaboration'. This addresses the issue of sharing your applications with external users.
Azure B2C, on the other hand, is mainly oriented to supporting customer transactions on customized applications. A fundamental difference with B2B is that it is not a feature of Azure AD, but rather a stand-alone service, although based on Azure AD technology.
And here we have the first key difference: Azure AD B2C is a separate service from Azure AD.
Yes, it's built on the same technology, but it's still distinct; instead, Azure AD B2B is actually a feature of Azure AD. In B2B, external users keep their original identity, but a reference object is created in the Azure AD tenant (now Microsoft Enter ID) of the host organization. In B2C, the customer user will be managed in a separate B2C AD.
In B2C it is possible to federate users from other identity providers (including Entra ID), so not all users are necessarily “managed” directly in the B2C tenant and some may only be referenced while their main identity remains in the source system.

B2C is also an authentication solution, but it is not oriented to sharing access like B2B, but is intended for end users. Azure AD B2C takes the authentication process to a higher level, improving security through customized policies that allow you to control how customers register and access applications.
And here we have the second fundamental difference: the user management factor is completely different. With Azure AD B2B, the host has total control of the system, while with Azure AD B2C, customers have the ability to manage their profiles within the limits defined by the organization.
The last key difference concerns what forms of identities are supported and where they are managed. With Azure AD B2B, the system is accessible to any employee, vendor, and partner with work accounts. These accounts are all managed together in a single large directory.
As for Azure AD B2C, on the other hand, we have seen how accounts for local applications or from external identity providers such as Facebook and LinkedIn, as well as independent trust federations, are also supported for users. These accounts are managed through the application directory and are separated from any external directory.
Before using any cloud-based service, it's helpful to have an understanding of the service's cost model. Fortunately, to get started with a new app, Azure Active Directory B2C it is very affordable and will not involve any initial costs.
In fact, in addition to the two premium tiers of the service, Microsoft also provides a Free tier that offers a series of free features to help organizations manage user authentication in their applications and is particularly useful for startups or small businesses that want to test and scale their identity management system before moving to a paid plan.
This includes up to 50,000 monthly active users (MAU) at no additional cost, allowing businesses to start implementing scalable and customized identity solutions. In the free level, it is also possible to use essential features such as authentication with social identity (e.g. Google, Facebook) and the basic personalization of the login and registration pages to adapt them to your brand, with the possibility of modifying logos, colors and texts. Once the free threshold of 50,000 MAU (Monthly Active Users, the unit used to calculate service prices) has been exceeded, however, costs apply per additional monthly active user.
As for the two Premium tiers (called P1 and P2), the first includes all the features of the Free tier, adding support for advanced MFA (such as SMS or phone calls), Azure AD Identity Protection and conditional access, which allows you to define risk-based rules to improve access security. In addition, it offers advanced reporting capabilities and the ability to integrate on-premise applications, making it suitable for organizations that need a higher level of access control.
The Premium P2 plan further extends the capabilities of P1 with advanced tools for Privileged Identity Management (PIM) and more sophisticated protection through Azure AD Identity Protection, which includes threat detection and risk management. This plan is designed for organizations that need a high level of governance, with more granular controls for managing access and preventing potential threats.
There are also other factors that may influence the price and result in reductions or additional costs:
The security of its digital infrastructures does not only concern the protection of its data and employees, but also the correct administration and protection of its customers' information through identity management tools that facilitate registrations and access and offer its customers and users personalized and secure access experiences.
If you need a solution that allows end users of our applications to register themselves, modify their profile or carry out multi-organizational logins, Azure B2C could be the answer to your problems and be the ideal choice when you need personalized branding in the access/registration processes of an application or a website.
So there's nothing left to do but invite you to try the potential of the service with the free tier and let the qualities of B2C speak for themselves to understand if it's really the right choice for your needs.
Azure AD B2C is a Microsoft service designed to manage the identities and access of an organization's external users, such as customers and partners. The platform makes it possible to implement secure and personalized login experiences for web and mobile applications, using a variety of authentication methods and at the same time offering extensive customization possibilities.
The main difference lies in the type of users and the objectives. Azure B2B is an Azure Active Directory feature designed to allow shared access to business resources by employees and partners. Instead, Azure B2C is a separate service that manages the identities of end customers, allowing them to access the organization's customized applications. In addition, in B2B, identities are managed in the same directory, while in B2C, each tenant is isolated.
No, even though Azure B2C is based on the same technology as Azure AD, it's a separate, stand-alone service. It does not automatically share users or resources with the corporate directory, unless specific federations or integrations are configured.
Azure B2C allows users to be authenticated through different methods, including local accounts with a username and password, social accounts such as those of Google or Facebook, federated corporate identities, multi-factor authentication with codes or dedicated apps, passwordless methods such as OTP or magic links, extended credentials with smart cards and certificates, in addition to the possibility of using advanced personalized criteria defined in XML.
A tenant is an isolated directory instance used to manage identities and permissions. In Azure B2C, each tenant is independent of the others and does not share data or resources, acting as a dedicated space in which to manage the identities of an organization's customers.
CIAM stands for Customer Identity and Access Management. It indicates the set of technologies and practices used by companies to protect customers' personal information and offer them secure and easy access to digital services. An effective CIAM system increases security, improves the user experience, and ensures compliance with data protection regulations.
User flows are predefined processes that determine the behavior of user interactions with the authentication system, such as registration or password recovery. They are configurable from the Azure portal and can be customized in terms of fields to collect, graphic style and subsequent actions. If your needs are more complex, you can adopt customized criteria.
Yes, Azure B2C allows Single Sign-On, allowing users to authenticate once to access multiple connected applications. This improves the user experience, reduces the number of credentials to remember, and helps strengthen overall security.
Azure B2C provides a pricing model based on the number of monthly active users. There is a free tier that includes up to 50,000 monthly active users and basic features such as social authentication. Premium P1 and P2 plans add advanced features such as MFA with SMS or calls, identity protection, conditional access, and privileged identity management. Costs may also vary based on the use of customized policies or MFA methods that consume more resources.
Yes, thanks to the free tier that includes a generous volume of monthly users and essential features, Azure B2C represents a scalable and affordable solution even for startups and small businesses that want to test or launch a secure identity management system.
The Infra & Security team focuses on the management and evolution of our customers' Microsoft Azure tenants. Besides configuring and managing these tenants, the team is responsible for creating application deployments through DevOps pipelines. It also monitors and manages all security aspects of the tenants and supports Security Operations Centers (SOC).