In July 2025, a zero-day vulnerability affected hundreds of on-premises SharePoint servers around the world, allowing cryptographic keys to be stolen. In just a few hours, the 'ToolShell' exploit put the security of many organizations at risk. Dev4Side was among the first to intervene. Thanks to a proactive approach and automated response framework, we have secured all of our customers within 24 hours. Here's how it went.

The SharePoint ecosystem has been shaken by a global zero-day attack, which takes the name of ToolShell (CVE-2025-5370).
This vulnerability allowed criminal groups to compromise on-premises SharePoint servers around the world, using a simple unauthenticated POST to:
The problem therefore did not concern a single customer, but an entire category of companies still linked to local SharePoint infrastructures. As a result, the official patches were not enough, because, without a timely rotation of ASP.NET machine keys, the attackers could keep access even after the update.
In a flash, many of our customers found themselves dealing with a situation far beyond their reach:
In addition, several companies were using previous versions of SharePoint, such as SharePoint 2013 and 2010, which are no longer receiving updates, since they are now out of support.
For these infrastructures, the only solution was to migrate to SharePoint Online.
Despite the confusion generated between companies and IT departments, the ToolShell attack therefore immediately made it clear that the security of SharePoint environments should no longer be based on traditional on-prem models.

ToolShell (CVE-2025-53770) is a zero-day vulnerability which recently affected the on-premises versions of SharePoint 2016, 2019 and Subscription Edition, allowing remote code execution without authentication.
The attack then relied on a manipulated request to an internal SharePoint page (ToolPane.aspx), capable of bypassing security controls simulating legitimate access.
Once inside the system, the attacker can:
But what makes ToolShell dangerous is its ability to hit any SharePoint server exposed on the internet, regardless of the configurations set up or any errors on the part of the users.
In practice, all it takes is for the system to be online and out of date to be vulnerable.
The first case of attack was detected on July 7, 2025.
Within a few days, the exploit was published on GitHub and began to spread rapidly.
On July 19, Microsoft confirmed the existence of the attack and assigned official CVEs.
However, emergency patches were released only on July 21, when more than 85 organizations were already compromised.
When Microsoft confirmed the existence of ToolShell, our team was already operational. Thanks to an automated response framework and a deep understanding of SharePoint environments, we were able to secure all our customers in less than 24 hours.
Our intervention was divided into several phases, coordinated by a tried and tested emergency playbook:
However, we did not stop at managing the emergency.
We have transformed the crisis into an opportunity, to accelerate the transition to a more resilient SharePoint environment. We have therefore proposed to each customer a migration path to SharePoint Online, divided into three support phases:
Thanks to the cloud, our customers today operate on a more secure platform, which has led to a 42% reduction on total cost of infrastructure management, with peaks that in some cases have exceeded 90%.
And that was only the first noteworthy result.
We'll talk more about it in the next section.
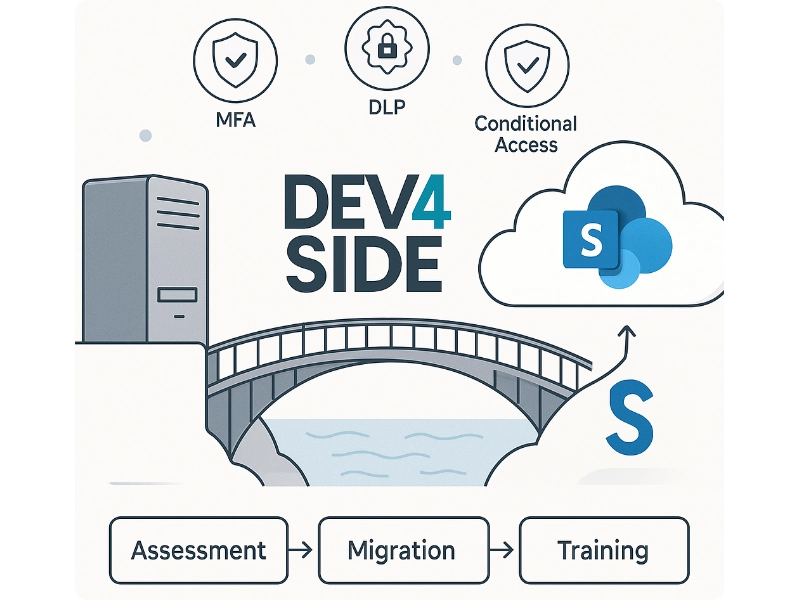
While we were all in a state of general emergency, Dev4Side was able to provide customers with full and timely protection.
As the number of companies compromised at the time of public disclosure grew, none of the companies we manage have been violated.
This result was possible thanks to a methodical intervention, which made it possible to:
But other important results have emerged in the medium term. Thanks to the migration path to SharePoint Online, in fact, our customers were able to:
Let's see the data collected on a typical infrastructure (5 servers, 5,000 users).
The Modern Work team specializes in developing and integrating custom solutions across the entire Microsoft 365 ecosystem. We design native applications for Microsoft and Azure platforms, and we implement business processes that maximize the return on investment in Microsoft 365.